Using Nmap with Wireshark
Author: Carmelo C.
Published: Sep 29, 2025hacking
networking
nmap
wireshark
This is an analysis of the states returned by Nmap when scanning a host or a subnet. The focus will be on:
- filtered
- closed
- open
Port Scanning Basic chapter of the Nmap Scanning Guide describes the states above as:
- filtered: Nmap cannot determine whether the port is open because packet filtering prevents its probes from reaching the port. The filtering could be from a dedicated firewall device, router rules, or host-based firewall software…
- closed: A closed port is accessible (it receives and responds to Nmap probe packets), but there is no application listening on it…
- open: An application is actively accepting TCP connections, UDP datagrams or SCTP associations on this port…
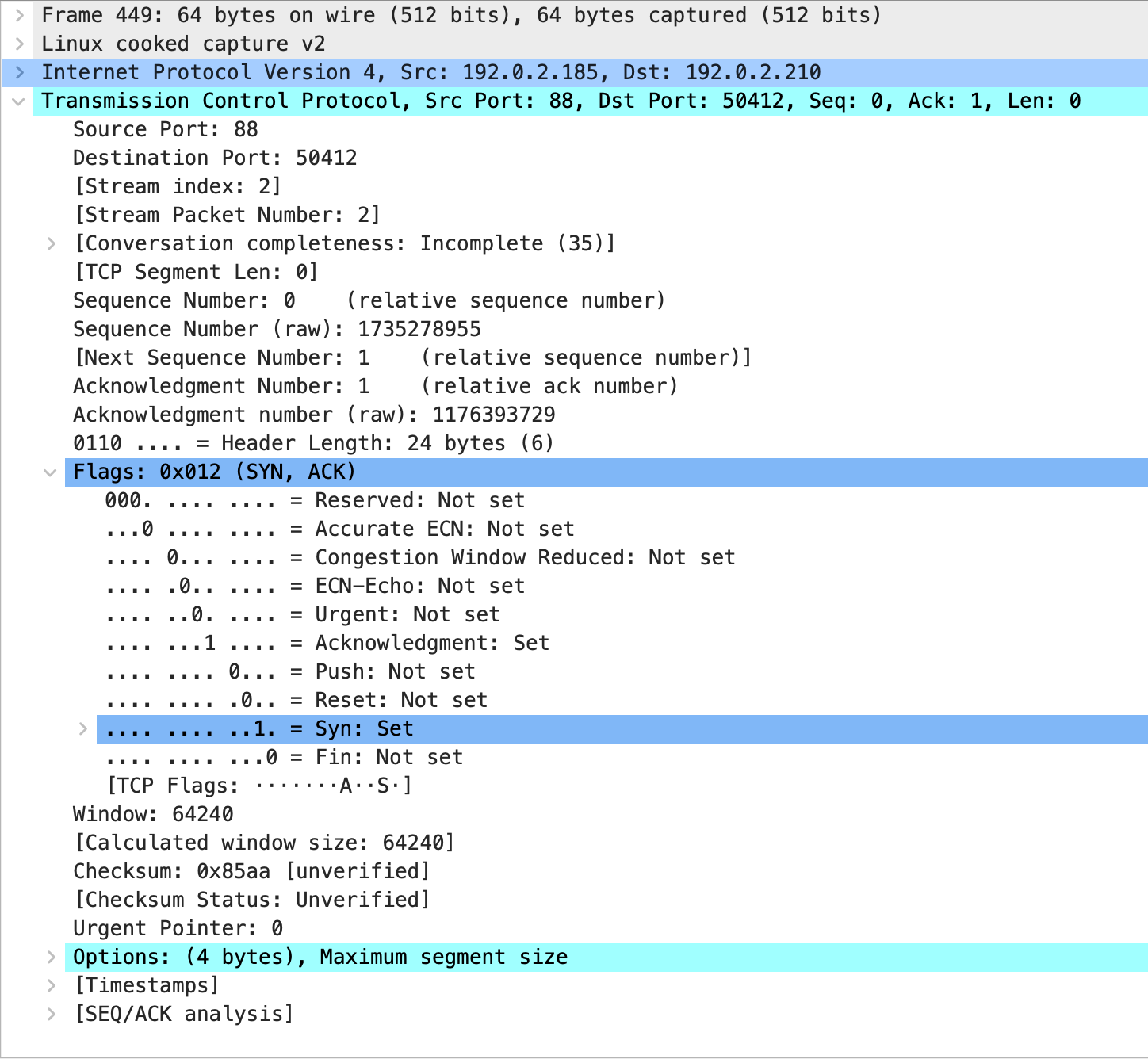
As port scanning is based on TCP three-way handshake it is both important and interesting to take a look at the information being exchanged on the wire by the hosts participating in the communication.
When our target is protected by, for instance, a firewall the port will not respond at all: it is filtered. Any probes sent by Nmap will either not receive a response or some ICMP codes (type 3, code 1, 2, 3, 9, 10, or 13) will be returned. The picture below shows the packet being sent (source = 192.0.2.210, destination = 192.0.2.185, port = 21).
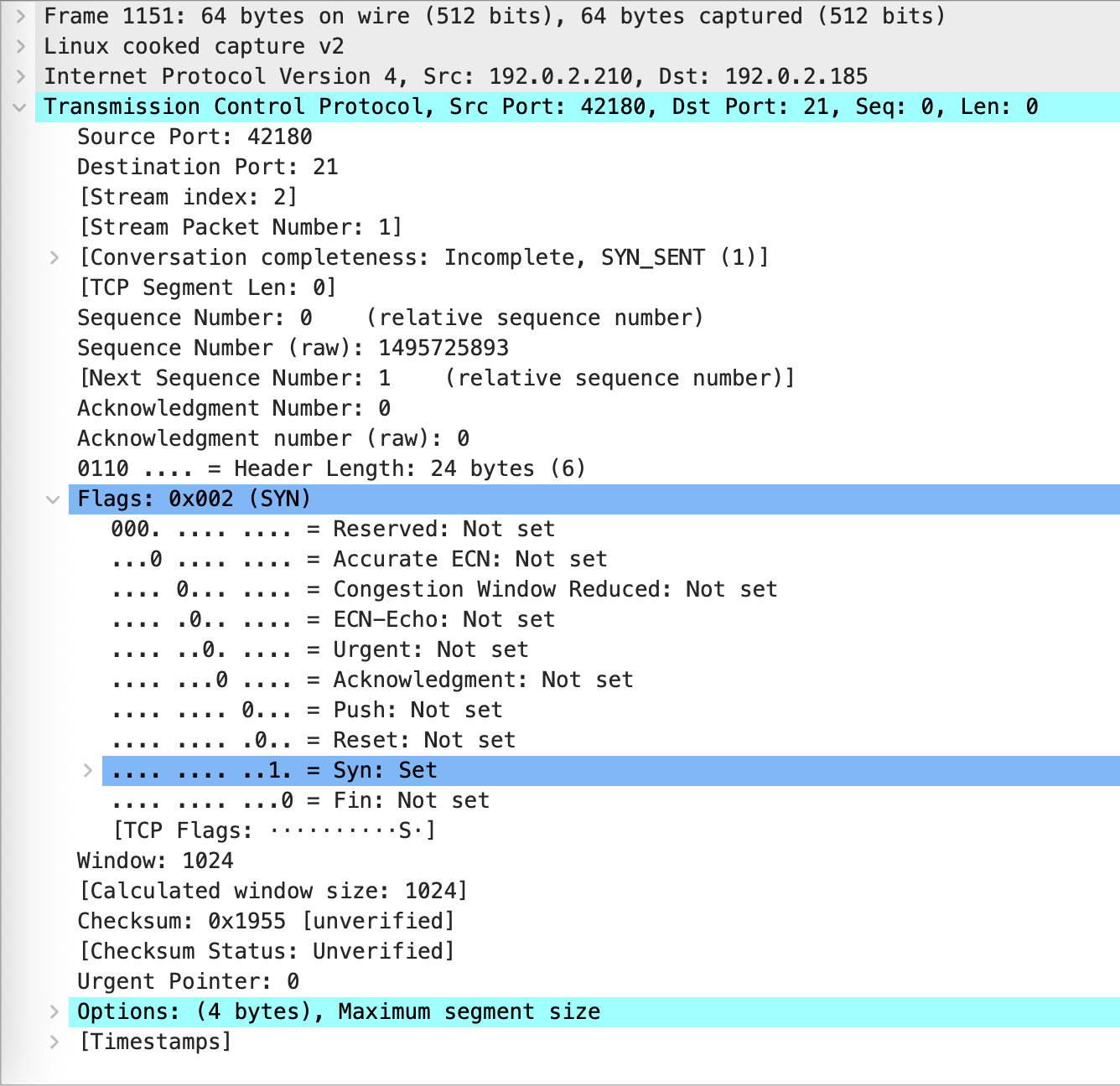
In the lucky event that the target, as in our lab, is reachable but no application is listening on the port, hence no communication can be established a
RSTpacket will be sent back in response to ourSYNprobe. The port is said to be closed. Please, notice how the response packet comes from port21(the target port).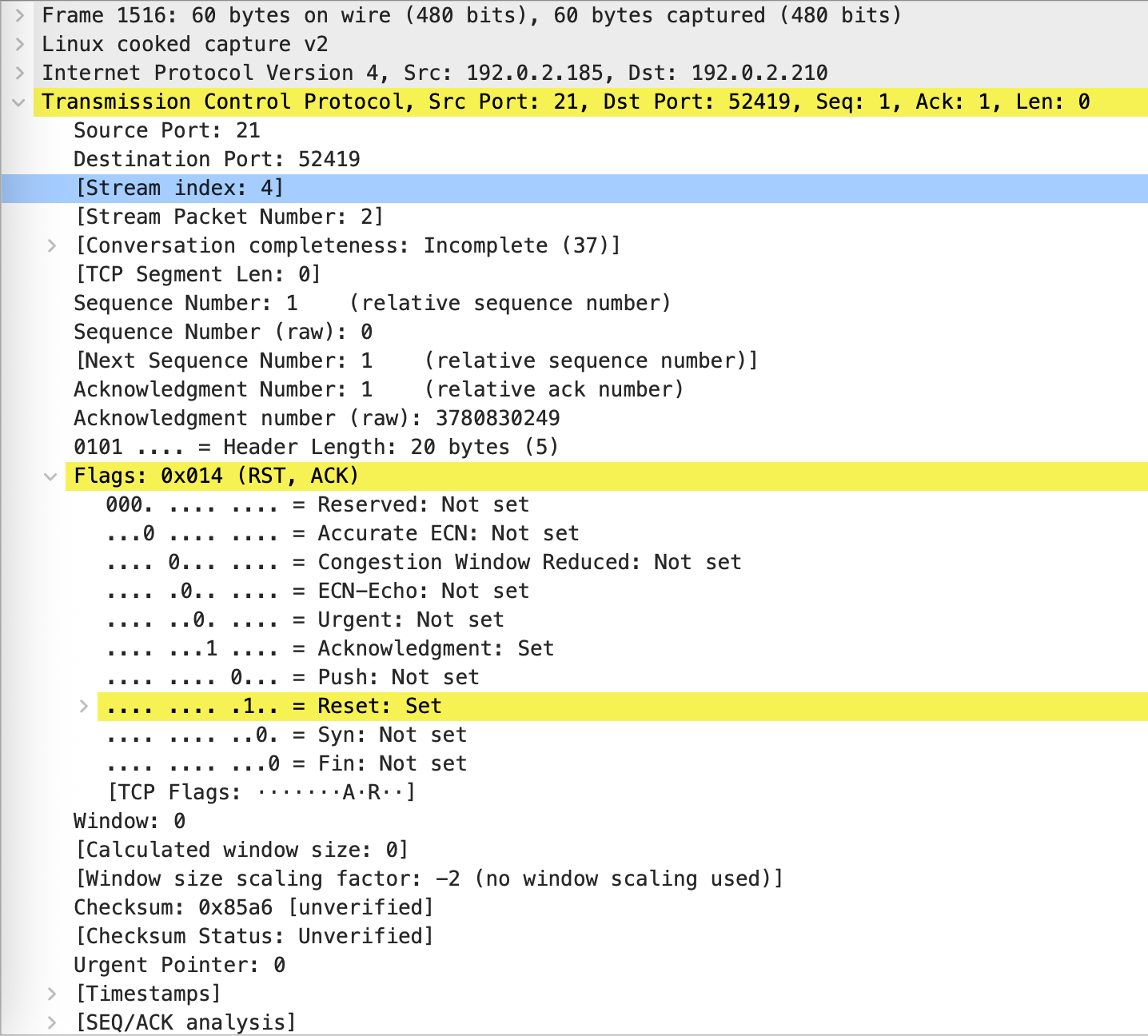
Finally, in case of an open port, the expected
SYN-ACKresponse is received. Nmap immediately stops the conversation as there’s no need to communicate with the application.